Infrastructure 2 NIC's
For infrustructure, we will need:
- Oracle VM VirtualBox installed
- Any version of a Linux server (I will use AlmaLinux 9.5)
- A terminal capable of establishing an SSH connection (for example, PowerShell)
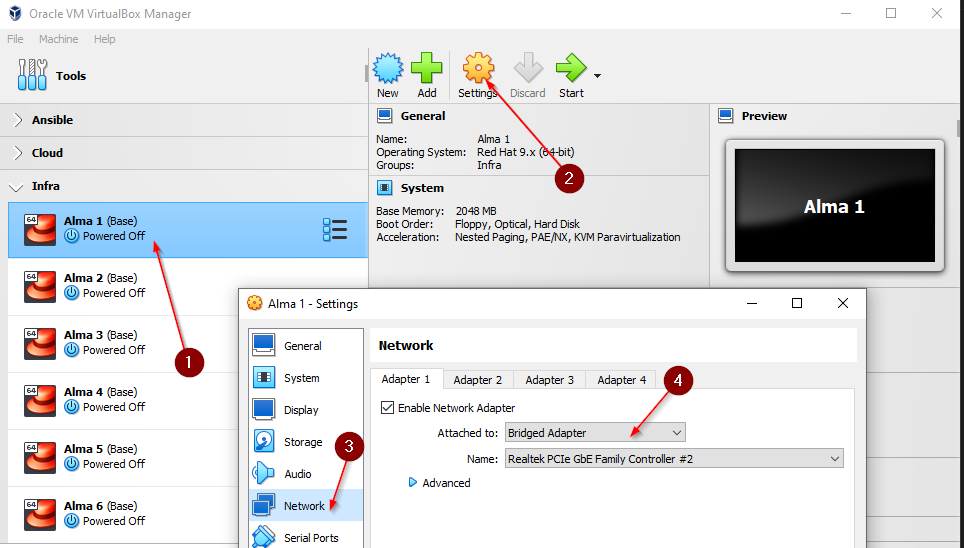
Set up the machine for the server 1:
- Click on the machine in VirtualBox.
- Go to Settings > Network.
- Under Adapter 1, set “Attached to” → Bridged Adapter.
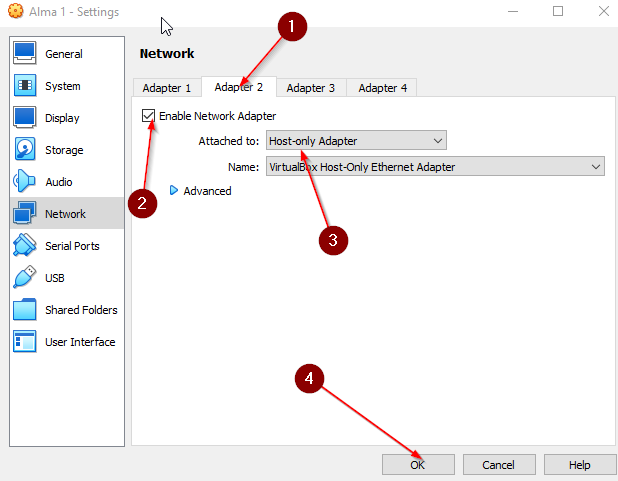
Add a second adapter (internal):
You should already have the settings window open.
- Go to Adapter 2.
- Check “Enable Adapter”.
- Set “Attached to” → Host-only Adapter.
- Click OK.
Set up the worker machines (servers 2-3):
Repeat the steps above for Adapter 1, but instead of selecting Bridged, choose Host-only Adapter. Do not enable a second adapter on these machines.
Observing IPs and Establishing SSH Connections
- Run your machines. New windows will open.
- Log in to your machines.
- Start with the load balancer machine.
- Type:
ip a
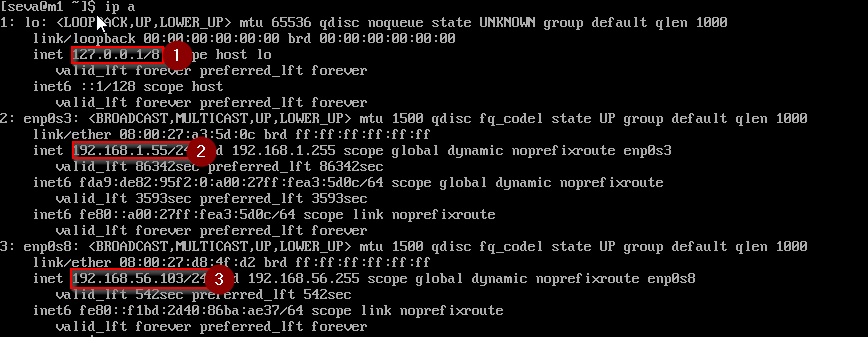
You will see three IP addresses:
- The first adapter is the loopback interface.
- The other two look similar. To determine which adapter is for internal vs. external use:
Type:
ip route
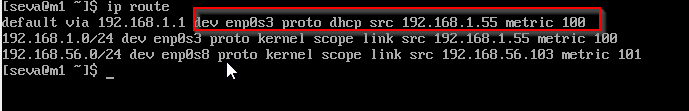
This shows that interface enp0s3 with IP 192.168.1.55 is used for internet traffic.
💡 Hint: Use Right Ctrl to switch between virtual terminals in VirtualBox.
Now log in to the other machines.
They should show only two interfaces:
- Loopback
- Internal network adapter
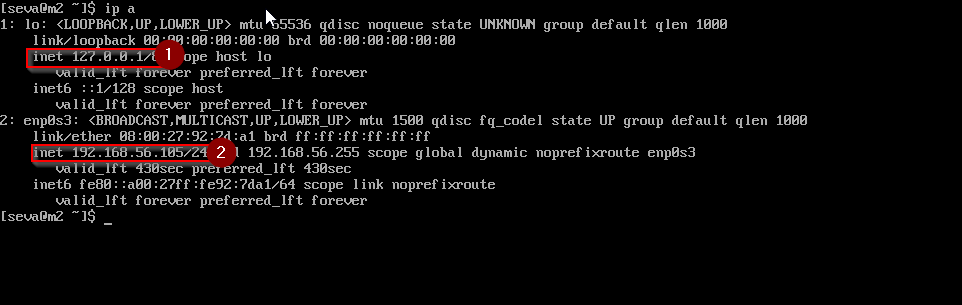
Establish SSH Connections (from your host)
To copy and paste more easily in terminal, open your terminal (PowerShell, cmd, embedded Mac terminal, or MobaXterm) and connect with:
ssh username@ip_address
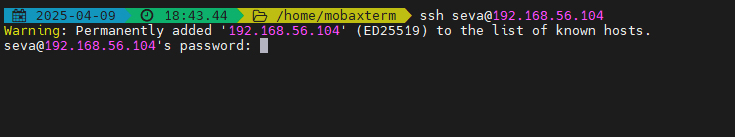
Repeat for each virtual machine/server 2-3.
Internet Connection for Worker Nodes
- Enable IP Forwarding on the Load Balancer
Allows Linux to forward packets between interfaces.
sudo vi /etc/sysctl.conf
Find or add this line:
net.ipv4.ip_forward = 1
Then apply the change immediately with:
sudo sysctl -p
You can verify:
cat /proc/sys/net/ipv4/ip_forward
Output should be: 1
2. Assign Interfaces to Zones
sudo firewall-cmd --permanent --zone=internal --change-interface=enp0s3
sudo firewall-cmd --permanent --zone=trusted --change-interface=enp0s8
3. Enable NAT on the External Interface
Masquerading translates internal IPs to the external IP.
sudo firewall-cmd --permanent --zone=external --add-masquerade
4. Allow Forwarding Between Zones
sudo firewall-cmd --permanent --zone=external --add-forward
5. Apply the Changes
sudo firewall-cmd –reload
6. Configure Default Gateway on Worker Nodes (servers 2-3)
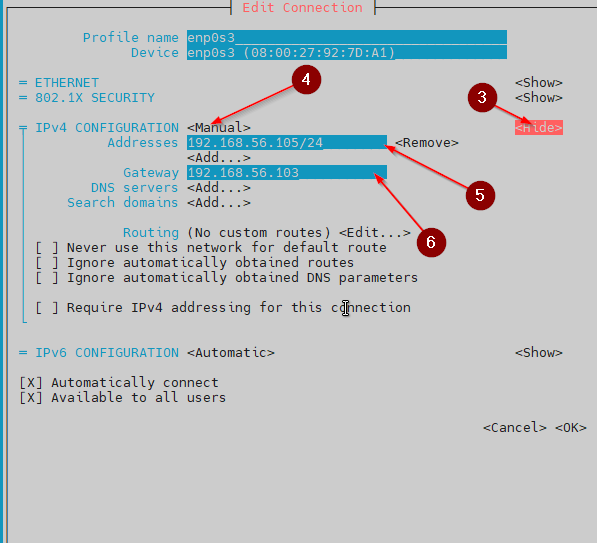
We’ll use nmtui for this:
sudo nmtui
- Choose Edit a connection.
- Select the active connection (likely the only one listed).
- Scroll down to IPv4 Configuration.
- Set the method to Manual.
- Enter your static IP (same as the one assigned earlier).
- Set the Gateway to the internal IP of the router/load balancer.
7. Reload the Network Connection
sudo nmcli connection down "enp0s3"; sudo nmcli connection up "enp0s3"
Final Step: Test Internet Access
Now, you should be able to access the internet from the worker nodes. Try:
ping 1.1.1.1
ping google.com